Cloud computing has revolutionized the way businesses operate, offering unprecedented flexibility, scalability, and access to cutting-edge technologies. However, the cost of cloud services—especially for CPU, GPU, and storage-intensive applications—can quickly escalate, leading to significant annual increases in expenses. For many businesses, a hybrid cloud approach, which combines on-premise infrastructure with cloud services, can provide an optimal balance between cost savings and operational efficiency. This article explores the benefits of a hybrid cloud environment and offers practical examples of how to implement it effectively.
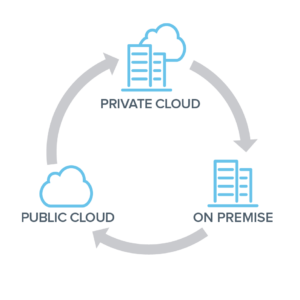
Understanding Hybrid Cloud Environments
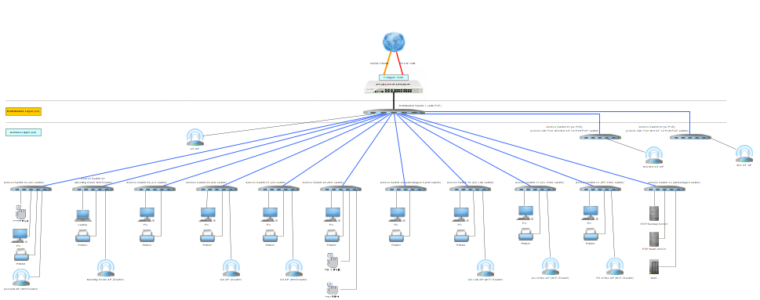
A hybrid cloud environment integrates private, on-premise infrastructure with public cloud services, allowing data and applications to move between the two environments. This approach provides the flexibility to run workloads in the most appropriate location based on cost, performance, and security requirements.
Benefits of a Hybrid Cloud Environment
1. Cost Savings
- Optimized Resource Allocation: Utilize on-premise resources for steady-state workloads and high-cost operations like GPU-intensive tasks, while leveraging the cloud for variable workloads and peak demand.
- Reduced Cloud Spending: Mitigate escalating cloud expenses by strategically deploying resources on-premise where it is more cost-effective.
2. Scalability and Flexibility
- Elastic Scaling: Seamlessly scale out to the cloud during peak times or for specific workloads that require additional resources.
- Flexible Workload Management: Easily move workloads between on-premise and cloud environments based on current needs and cost considerations.
3. Enhanced Control and Security
- Data Sovereignty: Keep sensitive data on-premise to comply with regulatory requirements and enhance security.
- Custom Security Measures: Implement tailored security measures on-premise while benefiting from robust cloud security for less sensitive data.
Implementing a Hybrid Cloud Environment: Key Considerations
1. Assess Workload Requirements
Evaluate your applications to determine which workloads are best suited for on-premise infrastructure versus the cloud. Consider factors such as:
- Resource Intensity: Identify CPU/GPU-intensive workloads that could incur high cloud costs.
- Data Sensitivity: Determine which data sets require stringent security and compliance measures.
Example: A financial services company might keep sensitive transaction processing on-premise while using the cloud for customer analytics and marketing campaigns.
2. Optimize On-Premise Infrastructure
Invest in modernizing your on-premise infrastructure to ensure it can efficiently handle the workloads you plan to run locally. This includes:
- Upgrading Hardware: Ensure you have the necessary compute, storage, and networking capabilities.
- Implementing Virtualization: Use virtualization technologies to improve resource utilization and management.
Example: A video rendering company could invest in high-performance GPUs and storage solutions on-premise to handle rendering tasks while utilizing the cloud for project management and collaboration tools.
3. Leverage Cloud Services Strategically
Utilize cloud services for workloads that benefit most from the cloud's scalability and advanced features, such as:
- Burst Capacity: Handle sudden spikes in demand without over-provisioning on-premise resources.
- Advanced Analytics: Access cloud-based AI and machine learning services to analyze large data sets.
Example: An e-commerce platform might use the cloud to handle traffic surges during holiday seasons and deploy AI-driven recommendation engines for personalized shopping experiences.
4. Implement Robust Management and Monitoring Tools
Deploy tools that provide visibility and control over both on-premise and cloud environments. This ensures efficient resource utilization and cost management.
- Unified Management Platforms: Use platforms like VMware Cloud Foundation or Microsoft Azure Arc to manage hybrid environments seamlessly.
- Monitoring and Analytics: Implement monitoring tools to track performance, usage, and costs across both environments.
Example: A manufacturing firm could use a unified management platform to monitor production workloads on-premise while tracking supply chain analytics in the cloud.
5. Ensure Seamless Integration and Interoperability
Ensure that your on-premise and cloud environments can work together seamlessly. This involves:
-
Hybrid Cloud Architecture: Design your IT architecture to support hybrid deployments, including network connectivity and data integration.
-
APIs and Middleware: Use APIs and middleware solutions to facilitate communication between on-premise and cloud-based applications.
Example: A healthcare provider might integrate on-premise electronic health record (EHR) systems with cloud-based patient engagement platforms to provide a cohesive patient experience.
Practical Examples of Hybrid Cloud Implementations
1. Media and Entertainment
Scenario: A film production company needs significant GPU resources for rendering but only during post-production phases.
Hybrid Solution: The company invests in high-performance GPU servers on-premise for rendering tasks while using the cloud for collaboration and file sharing among global teams.
2. Retail
Scenario: An online retailer experiences high variability in web traffic, especially during sales events.
Hybrid Solution: The retailer runs the core e-commerce platform on-premise to ensure performance and cost predictability. During peak times, it scales out to the cloud to handle additional traffic and uses cloud-based AI services for customer insights and targeted marketing.
3. Healthcare
Scenario: A hospital needs to maintain strict control over patient data but also wants to leverage cloud-based analytics for operational efficiency.
Hybrid Solution: The hospital keeps patient records and critical applications on-premise to comply with data protection regulations. It uses cloud services for non-sensitive data analytics, such as resource management and operational efficiencies.
Conclusion
A hybrid cloud environment offers the best of both worlds: the control and cost savings of on-premise infrastructure combined with the flexibility and scalability of cloud services. By carefully assessing workload requirements, optimizing on-premise resources, strategically leveraging cloud services, implementing robust management tools, and ensuring seamless integration, businesses can achieve a balanced, efficient, and cost-effective IT strategy.
Embracing a hybrid cloud approach allows businesses to adapt to changing demands, manage costs effectively, and maintain control over critical data and applications. As cloud technology continues to evolve, the hybrid model provides a pragmatic and forward-thinking solution to the complexities of modern business IT needs.





 Archsolution Limited
Archsolution Limited