There are a number of articles being written for small businesses and will be published.
During the Coronavirus crisis since 2020, there are lots of people working at home remotely. In the first article, it is going to discuss communication tools for remote work. WhatsApp / WeChat, etc. are not classified as communication tools for work and not to be discussed in this article. However, there are still lots of tools needed to be in-place like Remote Access, Sharing of document, etc. We will discuss them later in other articles with tips.
There are many software able to do video conferencing with both freemium and paid software. It is important for this type of software with features below:
- Screen Sharing
- File Sharing
- WebCam Connection
- Computer Audio Connection (Mic+Speaker/ Headset)
- Options for toll-free diag-in
- Options for recording
We would like to introduce some of the choices as below:
1. Google Hangouts
Let’s start with freemium first. This is again a free tool provided by the giant – Google. You can just type Google hangouts at google search. On the left hand side, you will see your contact list at the left hand side. Then, you can invite anyone to join the call.
 2. Zoom
2. Zoom
Zoom is now the most popular conference call or even webinar services in the world. You can use Zoom free under some limitations like 40 minutes for multiple participants. However, you can also pick paid services with options to provide toll free calls across 100 countries with a lower price than WebEx.
Unfortunately, more users found that it is possible to expose the meeting to strangers without setting the security carefully. Also, Zoom had shared the meeting information with servers located in China. It is very sensitive for information leakage due to the American Chinese founder. In APR 2020 (latest update), they have fixed their security issues.
3. WebEx
For me, it is still the number one in the market with its stability and security. However, it is still one of the most expensive one. For user outside UK or US, the price is extremely high for those corporations seeking with toll-free support.
Furthermore, Cisco WebEx is the pioneer for providing video conference solutions with the best security. So, it is better for businesses with higher budget.
4. Jitsi Meet
This is an Open Source solution. You can use their service freely at
https://meet.jit.si with starting a meeting room. Even anyone could start a meeting, but you can have your own password for the target participants to reach the unique meeting room for privacy & protection.
Also, you can have a choice to host the Jitsi at your own server and add security protection like authorized account to start a meeting. As many other open source solution, it is possible to integrate your own LDAP server for installation on-premises. We can help you or your organization to
set up Jitsi-meet server with a very low charge.
5. Microsoft Teams
If you are using office 365, you may have Microsoft Teams to connect to your team members or making calls. If you have Microsoft Teams available in your organization, you don’t need to shop around.
It is quite easy to manage and fully integrate with Microsoft Active Directory. For the functionalities, it is basically similar to WebEx but in a different user interface.
6. Others
There are other different vendors providing similar monthly subscription plans like Zoom or Cisco including:
To conclude, it is better to have a big vendor for more resources available for the underlying infrastructure being invested by the vendor. Basically, all of these solutions could be used in PC (Windows), MAC OSX and even mobile devices. However, Jitsi Meet is an alternative for not paying any service charges to have your own solution with internal IT resources. For small team, it is possible to pick Google Hangouts – freemium version.



 Archsolution Limited
Archsolution Limited

 2.
2.  Unfortunately, more users found that it is possible to expose the meeting to strangers without setting the security carefully. Also, Zoom had shared the meeting information with servers located in China. It is very sensitive for information leakage due to the American Chinese founder. In APR 2020 (latest update), they have fixed their security issues.
3.
Unfortunately, more users found that it is possible to expose the meeting to strangers without setting the security carefully. Also, Zoom had shared the meeting information with servers located in China. It is very sensitive for information leakage due to the American Chinese founder. In APR 2020 (latest update), they have fixed their security issues.
3.  Furthermore, Cisco WebEx is the pioneer for providing video conference solutions with the best security. So, it is better for businesses with higher budget.
4.
Furthermore, Cisco WebEx is the pioneer for providing video conference solutions with the best security. So, it is better for businesses with higher budget.
4.  Also, you can have a choice to host the Jitsi at your own server and add security protection like authorized account to start a meeting. As many other open source solution, it is possible to integrate your own LDAP server for installation on-premises. We can help you or your organization to
Also, you can have a choice to host the Jitsi at your own server and add security protection like authorized account to start a meeting. As many other open source solution, it is possible to integrate your own LDAP server for installation on-premises. We can help you or your organization to  It is quite easy to manage and fully integrate with Microsoft Active Directory. For the functionalities, it is basically similar to WebEx but in a different user interface.
6. Others
There are other different vendors providing similar monthly subscription plans like Zoom or Cisco including:
It is quite easy to manage and fully integrate with Microsoft Active Directory. For the functionalities, it is basically similar to WebEx but in a different user interface.
6. Others
There are other different vendors providing similar monthly subscription plans like Zoom or Cisco including:
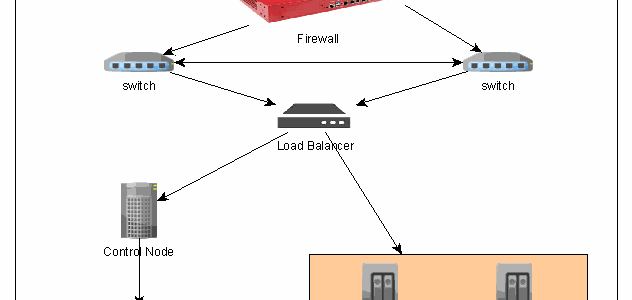
 Figure 1: Open Stack – Architecture for the Private Cloud in Archsolution Limited
For hardware, they are basically listed below:
Figure 1: Open Stack – Architecture for the Private Cloud in Archsolution Limited
For hardware, they are basically listed below:
 Figure 2: Open Stack architecture – for a data science consulting company
The data science consulting company is aimed to build their own private cloud with open source technology for research and training purposes. There are some vital R&D projects like IoT and AI running in this platform.
If it is required to have HADR, it is just needed to duplicate 1 set to another data center with the synchronization to maintain the information stored at near real-time basis.
For the management of Open Stack cloud, we use chef and compass to maintain the daily operation for the private cloud. With the continuous development of Open Stack framework and improvement in different Linux distro, Open Stack is now a reliable and scalable platform without any software investment like VMWare / Citrix / Microsoft, etc. Thus, this is a promising solution for enterprise with HADR features and live deployment of VMs. All-in-all, the private cloud solution should be a good answer for the public cloud security concerns and also the flexibility & scalability within a corporate environment.
Figure 2: Open Stack architecture – for a data science consulting company
The data science consulting company is aimed to build their own private cloud with open source technology for research and training purposes. There are some vital R&D projects like IoT and AI running in this platform.
If it is required to have HADR, it is just needed to duplicate 1 set to another data center with the synchronization to maintain the information stored at near real-time basis.
For the management of Open Stack cloud, we use chef and compass to maintain the daily operation for the private cloud. With the continuous development of Open Stack framework and improvement in different Linux distro, Open Stack is now a reliable and scalable platform without any software investment like VMWare / Citrix / Microsoft, etc. Thus, this is a promising solution for enterprise with HADR features and live deployment of VMs. All-in-all, the private cloud solution should be a good answer for the public cloud security concerns and also the flexibility & scalability within a corporate environment.